- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Phrack Magazine: Digital hacking magazine.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
Tuesday, June 30, 2020
12 Hacking Websites & forums - Underground hacker sites
Thursday, June 11, 2020
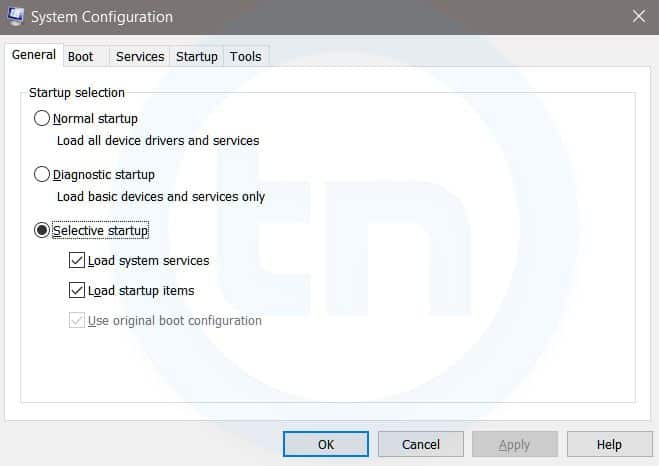
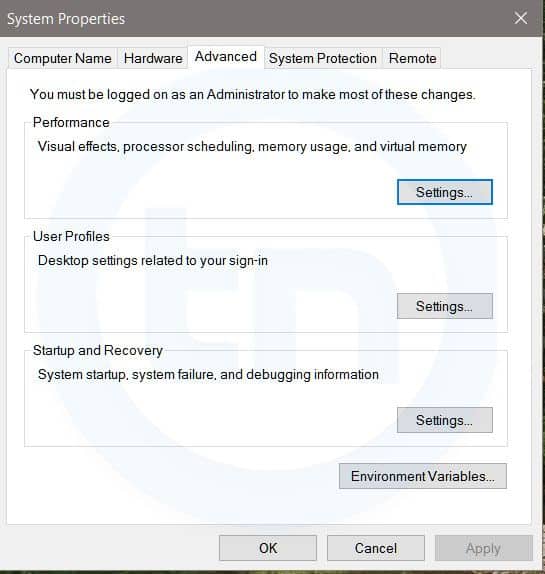
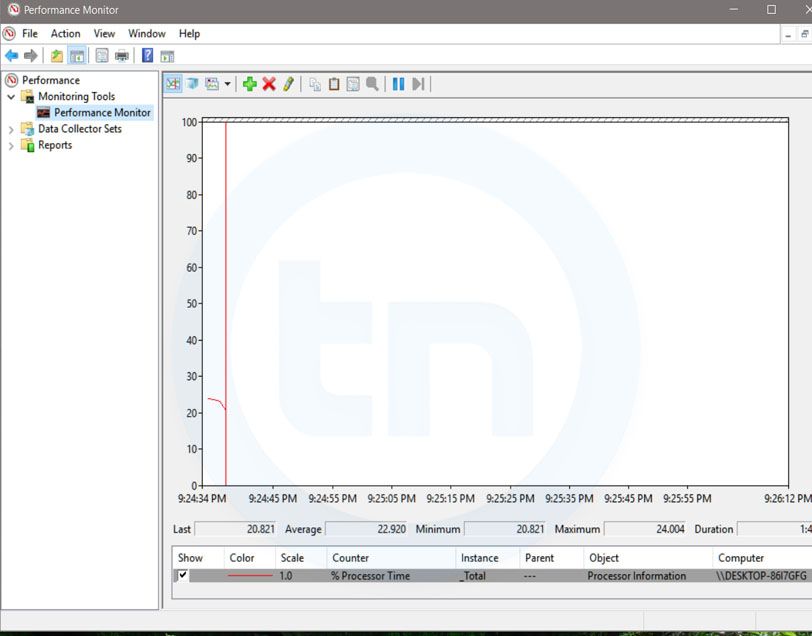
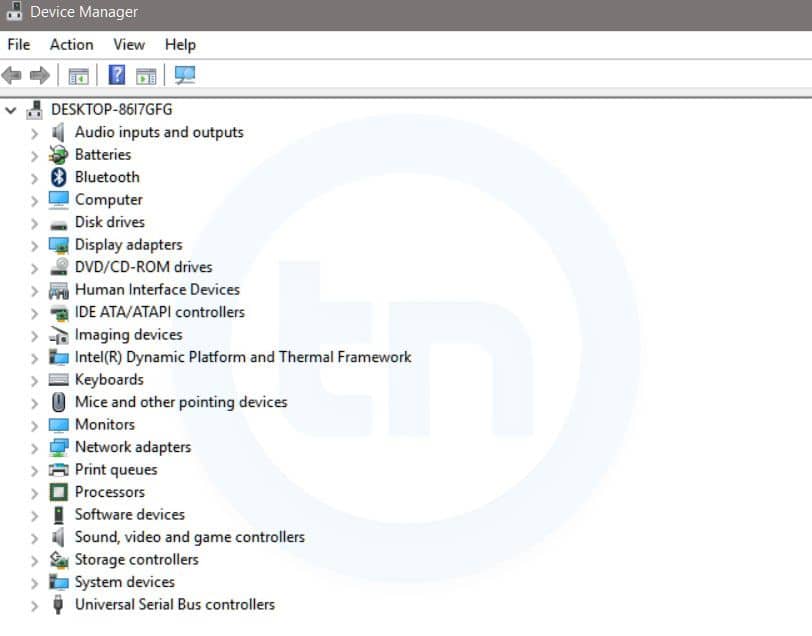
15 Important Run Commands Every Windows User Should Know
Important Run Commands Every Windows User Should Know
Top 20 Best Free Hacking Apps For Android |2019|
20 Best Free hacking apps For Android |2019|.
Android is now one of the most popular operating systems. So, hackers have also started using Android devices for their tasks. Now Android devices are used for penetration testing and other hacking activities including IT security administrator, Wi-Fi hacking and network monitoring. There are several hacking apps or Android devices. So, we have curated a list of best hacking apps for Android.
Before you start using these apps, you must take a backup of your important data. I also recommend the use of these apps on a separate device. Using this on your primary phone is not recommended. It is because many of these apps require a rooted device and app can also harm your phone.
Note: Hacking apps can be used for educational and malicious purpose. But we never encourage malicious operations. We are listing the apps here just for educational purpose. You should only use these apps to learn. We do not support any unethical use of these apps.
1. AndroRAT
AndroRAT stands for Android RAT. RAT is the short form of Remote Administrative Tool and it allows an attacker to remotely control and fetch information from a device. AndroRAT does the same thing. It has a server developed in Java/Swing but the Android application has been developed in Java Android.
AndroRAT allows you to connect information like call logs, contacts, messages, location and more. You can remotely monitor sent and received messages send texts, use the camera, open a URL in the browser, make phone calls and remotely monitor the device.
The connection to the server can be triggered by an SMS or a call. From the server GUI, you can check all the connected clients and access information.
As the app allows silent remote access, it is not available on Play Store.
2. zANTI
zANTI is a known penetration testing suite of applications you can install locally on Android smartphone. This tool brings scanning tools Diagnostic features and Reporting tools. You can use this malicious software to attack a network and check for any loopholes in your network. This tool is used to test redirect and SSL stripping attacks. You can edit request and response messages from web servers, the host takes websites from your Android phone and more.
3. FaceNiff
FaceNiff is another good Android hacking that allows you to intercept the traffic of your WiFi network. You can use this tool to snoop what people are doing on the network you are. You can snoop on services like Facebook, Twitter, Amazon, YouTube and more. This is one of the notable too for steal cookies from the WiFi network and gives the attacker unauthorized access to other people's account.
This app requires a rooted device. So, you can only use the app if you have a rooted phone.
4. Droidsheep
Droidsheep is also a similar app that helps security analysts understand what is happening in your Wi-Fi network. Like Face Sniff, this app can also hijack the web session profiles over a network and supports most of the services and websites.
The primary difference between Droidsheep and FaceSniff is that Droidsheep works with almost all the websites while FaceSniff has limited support.
5. Hackode
Hackode is another good hacking apps for Android. It is not a single app but a collection of tools for ethical hackers and penetration testers. The app comes with three modules including Reconnaissance, Scanning and Security Feed. You can use this app for SQL Injection, Google hacking, MySQL Server, Whois, Scanning, DNS Dif, DNS lookup, IP, MX Records, Security RSS Feed, Exploits etc.
The app is still in beta, but available in Play Store.
6. cSploit
cSploit is also a good security tool for Android. It comes with several options like cracking Wi-Fi password, installing backdoors, finding vulnerabilities and their exploits. If you are looking for a good hacking app or hacker app for Android, you should try this one for sure.
7. DroidBox
DroidBox is also a similar kind of app that allows you to do the dynamic analysis of Android applications. You can use this app to get information like hashes of APK package, network traffic, SMS & phone calls, Incoming/outgoing network data, Listing broadcast receivers and more.
8. Nmap
If you are into security or hacking, I am sure you already know the name of this too. Like the desktop tool, Nmap for Android also allows you to scan
It works on both on non-rooted and rooted phones. If you are a beginner, you should try this app and learn from it.
9. SSHDroid
SSHDroid is SSH tool developed for Android. It lets you connect to a remote computer and run terminal commands, transfer and edit files. The app also provided features like shared-key authentication, WiFi autostart whitelist, extended notification control etc,
This app is available on Play Store.
10. Kali Linux NetHunter
Kali Linux NetHunter is an open source penetration testing platform for Android. It officially supports Nexus and OnePlus devices. It provides the ultimate penetration testing platform that allows you to perform a wide range of attacks.
11. APKInspector
APKInspector allows you to perform reverse engineering on an APK. you can use this to get a deep insight or APK and get the source code of any Android app. You can do modifications in the APK and visualize the DEX code to erase the credits and license.
12. Shark for Root
Shark for Root is an advanced hacking tool for security experts and hackers. It can work as a traffic snipper. You can use the tcpdump command on rooted devices. It works on Wi-Fi, 3G, and FroYo tethered mode.
13. dSploit
dSploit is an Android network penetrating testing suit. You can download and install it on your device to perform network security testing. It supports all Android devices running on Android 2.3 Gingerbread or higher. You need to root this phone for using the app. After rooting the phone, you need to download BusyBox from Google Play Store
The app comes with several modules including Port Scanner, Inspector, RouterPWN, Trace, Login Cracker, Packet Forger, Vulnerability Finder, and MITM.
14. WPScan
WPScan is a WordPress vulnerability scanner for Android. This app is used to scan WordPress based websites and find possible vulnerabilities. WPScan is a popular desktop tool but this WPScan for Android is not related to that. So, do not think of it as an official WPScan app.
15. Network Mapper
Network Mapper is a network scanner tool for network admins. It used to scan the network, lists all devices connected and find Open ports of various servers like FTP servers, SSH servers, SMB servers etc on the network. The tool is available on Play Store.
16. Andosid
Andosid is like LOIC for the desktop. This tool is used to perform DOS attacks from Android mobile phones. You can use this tool to set a target URL and perform a DOS attack in one click. The tool will start flooding target URL with fake requests.
17. DroidSQLi
DroidSQLi app allows attackers to perform SQL Injection on a target URL. You just need to find a target URL and this tool will start the fully automated SQL Injection attack.
18. AppUse
AppUse is a Virtual Machine developed by AppSec Labs. It is a freely available mobile application security testing platform that comes with lots of custom made tools by AppSec Labs. If you want to sue your Android phone as your penetration testing tool, this one is for you.
19. Network Spoofer
Network Spoofer is also a good hacking app for android. It lets you change the website on other people's computer from your Android phone. Connect to a WiFI network and then choose a spoof to use with the app. this tool is to demonstrate how vulnerable a network is. Do not try this on any unauthorized networks.
20. DroidSheep Guard
As the name suggests, DroidSheep Guard works against DroidSheep. It monitors Android devices' ARP-table and tries to detect ARP-Spoofing attack on your network. It does not require a rooted device.
@EVERYTHING NT
Amnesia / Radiation Linux Botnet Targeting Remote Code Execution In CCTV DVR Samples

| MD5 | SHA256 | SHA1 |
|---|---|---|
| 74bf554c4bc30d172cf1d73ac553d766 | 06d30ba7c96dcaa87ac584c59748708205e813a4dffa7568c1befa52ae5f0374 | 3c40221177383da576b11a0b3f6b35d68a9cde74 |
| 5dd9056e5ab6a92e61822b6c04afd346 | 10aa7b3863f34d340f960b89e64319186b6ffb5d2f86bf0da3f05e7dbc5d9653 | c865dd67853a24fd86ef74b05140827c1d5fd0bd |
| 2b486466f4d3e30f7b22d0bc76cb68f9 | 175fe89bbc8e44d45f4d86e0d96288e1e868524efa260ff07cb63194d04ea575 | ed62f6d1588bea33c20ababb42c02662d93d6015 |
| 3411bb2965f4c3d52c650aff04f48e52 | 1d8bc81acbba0fc56605f60f5a47743491d48dab43b97a40d4a7f6c21caca12a | 1e0281178b4a9d8dec74f50a7850867c87837435 |
| 34f915ac414e9aad2859217169f9a3aa | 2f9cd1d07c535aae41d5eed1f8851855b95b5b38fb6fe139b5f1ce43ed22df22 | d66f1e47c983a8d30ad7fd30cd08db8cd29a92b0 |
| 59e08f2ce1c3e55e2493baf36c1ad3c6 | 327f24121d25ca818cf8414c1cc704c3004ae63a65a9128e283d64be03cdd42e | 90d45b81e9a97ddcc9911122f4e8fd439ccc8fa9 |
| f4bc173bf80d922da4e755896af0db61 | 37b2b33a8e344efcaca0abe56c6163ae64026ccef65278b232a9170ada1972af | fab32f8c3ce3a837e80a1d98ada41a5bf39b01e7 |
| a253273e922ce93e2746a9791798e3fe | 3a595e7cc8e32071781e36bbbb680d8578ea307404ec07e3a78a030574da8f96 | 99cfdec405f6a9f43d58b1856fce7ca3445395d3 |
| 335e322c56278e258e4d7b5e17ad98e6 | 4313af898c5e15a68616f8c40e8c7408f39e0996a9e4cc3e22e27e7aeb2f8d54 | 504022707609a0fec9cbb21005cb0875be2a4726 |
| 93522e5f361a051f568bd1d74d901d30 | 46ea20e3cf34d1d4cdfd797632c47396d9bdc568a75d550d208b91caa7d43a9b | e7fc96b2a92888572de2539f227c9a6625449f83 |
| c86af536d87c1e5745e7d8c9f44fd25d | 4b0feb1dd459ade96297b361c69690ff69e97ca6ee5710c3dc6a030261ba69e0 | 6ef69a683913ae650634aedc40af8d595c45cb4f |
| 90c7c5e257c95047dbf52bbfbe011fd6 | 4db9924decd3e578a6b7ed7476e499f8ed792202499b360204d6f5b807f881b8 | 1c3a9be6ae9300aaad00fb87d5407ed6e84ec80b |
| 7c0528e54b086e5455ef92218ea23d03 | 5e6896b39c57d9609dc1285929b746b06e070886809692a4ac37f9e1b53b250c | 868abc912ff2fdcd733ff1da87e48e7d4c288a73 |
| 6405b42d2c7e42244ac73695bb7bfe6b | 64f03fff3ed6206337332a05ab9a84282f85a105432a3792e20711b920124707 | 173aca65181c8da84e062c803a43a404ad49302d |
| 6441157813de77d9849da5db9987d0bb | 6b2885a4f8c9d84e5dc49830abf7b1edbf1b458d8b9d2bafb680370106f93bc3 | 92dff9bdb31d3b9480d9e5f72a307715859dd094 |
| 614ea66b907314398cc14b3d2fdebe79 | 6b29b65c3886b6734df788cfc6628fbee4ce8921e3c0e8fc017e4dea2da0fd0b | c7e71c42d391f9c69375505dbf3767ba967f9103 |
| 00fe3120a666a85b84500ded1af8fb61 | 885dce73237c4d7b4d481460baffbd5694ab671197e8c285d53b551f893d6c09 | 342ed67e08d16ab982a4012fcecdca060a5da46b |
| 5477de039f7838dea20d3be1ae249fcb | 886136558ec806da5e70369ee22631bfb7fa06c27d16c987b6f6680423bc84b0 | 5b19202b45e5a58cadec8c2efa40fd924b64177d |
| 91bf10249c5d98ea6ae11f17b6ef0970 | 8f57ec9dfba8cf181a723a6ac2f5a7f50b4550dd33a34637cf0f302c43fd0243 | 682dab9ec3ff0b629cce4e16c9c74171dd2551d4 |
| fb0a7e12d2861e8512a38a6cdef3ddf0 | 9351ee0364bdbb5b2ff7825699e1b1ee319b600ea0726fd9bb56d0bd6c6670cb | c077c490bb22df9886475dc5bedfc6c032061024 |
| 9b7f5a1228fa66cbd35e75fb774fdc8e | 9c7a5239601a361b67b1aa3f19b462fd894402846f635550a1d63bee75eab0a2 | ae89bc6c5cc1818b3136a40961462327c3dececc |
| 5b97d54dc5001eb7cf238292405070a6 | a010bf82e2c32cba896e04ec8dbff58e32eee9391f6986ab22c612165dad36a0 | 96d2194f5f3927de75605f6ca6110fe683383a01 |
| 642f523bb46c2e901416047dca1c5d4e | ad65c9937a376d9a53168e197d142eb27f04409432c387920c2ecfd7a0b941c8 | bbf667213a446bc9bc4a5a2e54e7391752e3a9b8 |
| c617655312c573ecb01d292b320fff2e | aeb480cf01696b7563580b77605558f9474c34d323b05e5e47bf43ff16b67d6a | de102a6f35e08f18aa0c58358f5b22871eb0a45f |
| c8835a3d385162ae02bd4cb6c5ebac87 | b113ec41cc2fd9be9ac712410b9fd3854d7d5ad2dcaac33af2701102382d5815 | 831eb9cf0dcd57a879c04830e54a3b85fe5d6229 |
| 1497740fa8920e4af6aa981a5b405937 | b13014435108b34bb7cbcef75c4ef00429b440a2adf22976c31a1645af531252 | 8d6b90f0b88b1ad5dcc87d377e6a82dc6ac64211 |
| 5e925e315ff7a69c2f2cf1556423d5af | b3d0d0e2144bd1ddd27843ef65a2fce382f6d590a8fee286fda49f8074711545 | 64fe900b3a2b030c28211404afa45703c6869dea |
| 951ec487fb3fece58234677d7fe3e4dc | bdefa773e3f09cdc409f03a09a3982f917a0cc656b306f0ece3dd1a2564a8772 | 0b03d9471522590530dd90ad30b2d235ec98b578 |
| 3e84998197fc25cbac57870e3cdeb2de | c03b403d5de9778a2ec5949d869281f13976c2fc5b071e0f5f54277680c80902 | 0b9eb6d931dc6b226a913e89bb422f58228de0d0 |
| c3a73d24df62057e299b6af183889e6b | cb2382b818993ef6b8c738618cc74a39ecab243302e13fdddb02943d5ba79483 | 6a683ef6f7653e5ee64969cbbbe4403601ae9ded |
| d428f50a0f8cd57b0d8fe818ace6af20 | ce61dcfc3419ddef25e61b6d30da643a1213aa725d579221f7c2edef40ca2db3 | 9bd832256b94e43546dfb77532f6d70fcd1ce874 |
| e1d6d4564b35bb19d2b85ca620d7b8f2 | d0bda184dfa31018fe999dfd9e1f99ca0ef502296c2cccf454dde30e5d3a9df9 | c1af00d3263893b5d23dbf38015fe3c6a92cefaf |
| e9502ae7b0048b9ea25dd7537818904c | e7d6b3e1fba8cdf2f490031e8eb24cd515a30808cdd4aa15c2a41aa0016f8082 | 0e080ac0130ab3f7265df01b8397e4abd13c38cb |
| 8eb34e1fb7dd9d9f0e1fef2803812759 | eb54dc959b3cc03fbd285cef9300c3cd2b7fe86b4adeb5ca7b098f90abb55b8a | 5310a99f0f8c92bfa2f8da87e60c645f2cae305a |
| ca0fc25ce066498031dc4ca3f72de4b8 | f23fecbb7386a2aa096819d857a48b853095a86c011d454da1fb8e862f2b4583 | 7f4d97eea294fc567b058b09cc915be56c2a80e1 |
| 5a2fcfff8d6aab9a0abe9ca97f6093ed | f6af2fa4f987df773d37d9bb44841a720817ce3817dbf1e983650b5af9295a16 | f4ddf49fbf23edb23f50be62637a4a688e352057 |
| ed98e8fa385b39ca274e0de17b1007e6 | f7a737cb73802d54f7758afe4f9d0a7d2ea7fda4240904c0a79abae732605729 | a69d4c2b88bfe3a06245f8fbfb8abe5e9a894cec |
| 320db5f1230fcfe0672c8515eb9ddcfc | f7cf1e0d7756d1874630d0d697c3b0f3df0632500cff1845b6308b11059deb07 | 8d40dbf34a02dd43a81e5cdc58a0b11bfa9f5663 |
| 18d6af9211d0477f9251cf9524f898f3 | f97848514b63e9d655a5d554e62f9e102eb477c5767638eeec9efd5c6ad443d8 | b0e76be186fd609d5a8a33d59d16ffa3bdab1573 |
More articles
Wednesday, June 10, 2020
SMBleed: A New Critical Vulnerability Affects Windows SMB Protocol
via The Hacker News
Related articles
- Pentest Ubuntu
- Hacking Box
- Hacking Bluetooth
- Pentest Vs Ethical Hacking
- Pentestbox
- Pentest Cheat Sheet
- Pentester Academy
- Hacking With Python
- Pentest Reporting Tool
- Pentest Questions
- Hacker Attack
- Hacking Process
- Pentest Lab Setup
- Hacking Youtube
- Pentest Software
- Pentest Magazine
- Pentest Smtp
- Pentest Open Source
- Hackerrank Sql
Tuesday, June 9, 2020
Aircrack-ng: The Next Generation Of Aircrack
 "Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks." read more...
"Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks." read more...Website: http://www.aircrack-ng.org
How Block Chain Technology Can Help Fight Wuhan Corona Virus Outbreak
As the death toll and the infected cases of widespread coronavirus continue to increase, global organizations and the tech industry has come forward with technology like blockchain to fight coronavirus.
Along with the equipment and monetary support, technology also withstands against the virus with better plans and solutions. Hence, tech industries have started leveraging blockchain technology in the wake of a global health emergency.
Blockchain Helps In Real-Time Online Tracking
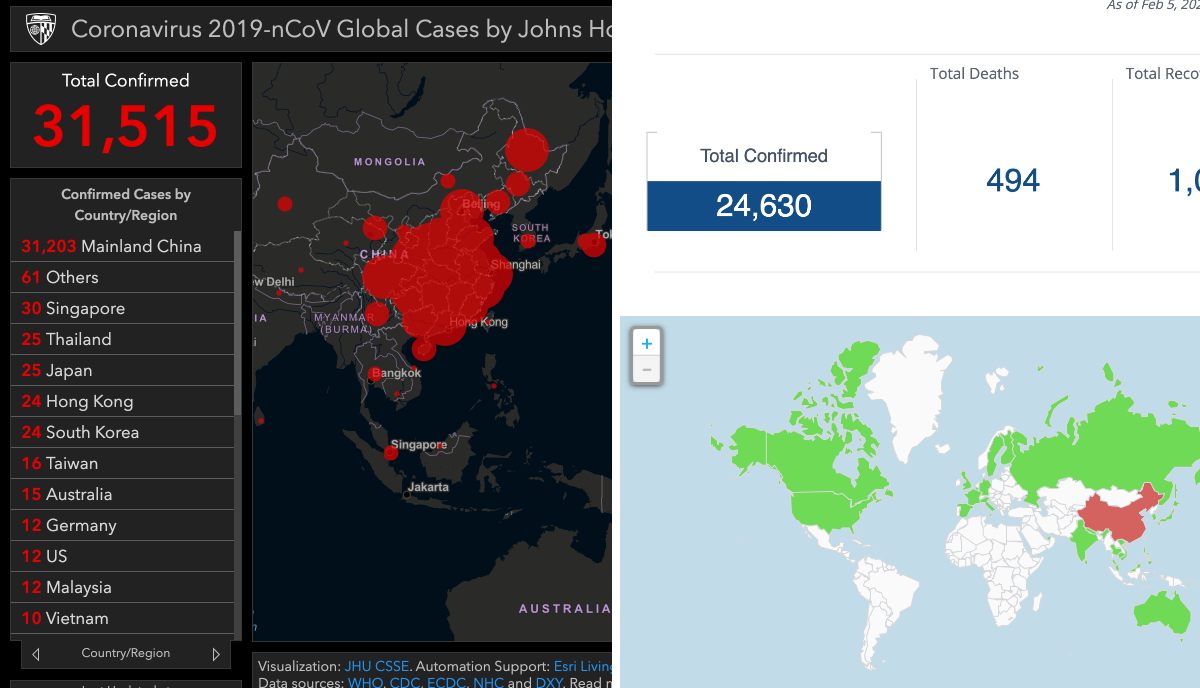
The Center for Systems Science and Engineering has already set up an online platform to track coronavirus and visualize the growing number of infected patients in real-time.
But Acoer, an Atlanta-based blockchain app developer, has also launched an alternative online data visualization tool to easily trail and depict the Cororanvirus outbreak using blockchain technology.
Acoer platform, named HashLog, is more advanced and clear as it pulls the data from the Hedera Hashgraph database using the HashLog data visualization engine.
Hedera Hashgraph is an immutable, transparent and decentralized database based on distributed ledger technology that provides synchronized and unchangeable data from the public networks.
Moreover, researchers, scientists, and journalists can use the HashLog dashboard to understand the spread of the virus and act against it swiftly.
For data sources, Johns Hopkins CSSE extracts data from WHO, CDC, ECDC, NHC, and DXY. On the other hand, Acoer maps the public data, including data from the Center for Disease Control (CDC) and the World Health Organization (WHO). Therefore, data may differ on both platforms.
Blockchain Can Help Monitor And Control Money Flow
To fight the further spread of the coronavirus (2019-nCoV) outbreak globally, China has also received abundant monetary support from the international community to create better action plans.
China's govt-led organization and charities are responsible for overseeing and utilizing the influx of money to research and generate a solution for coronavirus. But due to the lack of coordination and mismanagement among the various organization, money is not being laid out to curb the crisis.
Recently, a paper published by Syren Johnstone, from the University of Hong Kong, discusses the problems encountered by charities, in China and elsewhere. It argues that the present crisis should be seen as a call to arms.
Syren urges for a borderless solution with better management of donations and implementation using the emerging tech like Blockchain and Artificial Intelligence.
Keeping that in mind, Hyperchain, a Chinese company, also announced blockchain-based charity platform to streamline the donation from all over the world.
Since the Hyperchain platform is based on the blockchain, it offers more transparency among the sender and receiver of funds to bring trust and immutability to restrict the transaction data deletion.
Overall, Hyperchain improves administrative function for the money and also extends the logistics actions.
@HACKER NT
Related word
Hacking All The Cars - Part 2
Connecting Hardware to Your Real Car:
Video Walk Through Using Hardware on a Real Car
Hardware Used:
https://amzn.to/2QSmtyL
Get CANtact:
https://amzn.to/2xCqhMt
Get USB2CAN:
https://shop.8devices.com/usb2can
Creating Network Interfaces:
Summary:
Related articles
DMitry: Deepmagic Information Gathering Tool
 "DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux Command Line Application coded in C. DMitry has the ability to gather as much information as possible about a host. Base functionality is able to gather possible subdomains, email addresses, uptime information, tcp port scan, whois lookups, and more." read more...
"DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux Command Line Application coded in C. DMitry has the ability to gather as much information as possible about a host. Base functionality is able to gather possible subdomains, email addresses, uptime information, tcp port scan, whois lookups, and more." read more...Download: http://packetstormsecurity.org/UNIX/misc/DMitry-1.2a.tar.gz
Related links
Monday, June 8, 2020
Hacking All The Cars - Part 2
Connecting Hardware to Your Real Car:
Video Walk Through Using Hardware on a Real Car
Hardware Used:
https://amzn.to/2QSmtyL
Get CANtact:
https://amzn.to/2xCqhMt
Get USB2CAN:
https://shop.8devices.com/usb2can
Creating Network Interfaces:
Summary:
Related word
Ask And You Shall Receive
 |
Yes, I often obtain samples from various sources for my own research.
I am sometimes too lazy/busy to post them but don't mind sharing.
If you are looking for a particular sample, feel free to ask. I might have it.
Send MD5 (several or few samples). I cannot provide hundreds/thousands of samples or any kind of feeds. If you ask for a particular family, I might be able to help if I already have it.
Unfortunately, I do not have time to do homework for students and provide very specific sets for malware with specific features as well as guarantee the C2s are still active. Send your MD5(s) or at least malware family and I check if I have it :) If i have it, I will either send you or will post on the blog where you can download.
If you emailed me in the past and never got an answer, please remind me. Sometimes emails are long with many questions and I flag them to reply to later, when I have time and they get buried or I forget. It does not happen very often but accept my apologies if it happened to you.
Before you ask, check if it is already available via Contagio or Contagio Mobile.
1. Search the blog using the search box on the right side
2. Search here https://www.mediafire.com/folder/b8xxm22zrrqm4/BADINFECT
3. Search here https://www.mediafire.com/folder/c2az029ch6cke/TRAFFIC_PATTERNS_COLLECTION
4. Search here https://www.mediafire.com/folder/78npy8h7h0g9y/MOBILEMALWARE
Cheers, Mila



